WinHex 17.4 [more=Изменения..](please note that most changes affect the forensic edition of WinHex only, i.e. X-Ways Forensics)
Keyword Searches
Ability to conveniently run non-GREP index searches for search terms that contain spaces, just like in conventional searches. This is very important for names (e.g. "John Doe" or "XYZ Technology Ltd") and spaced compound words (e.g. "bank account" or "credit card limit"). New index only.
This works even if the individual components of the compound already exceed the maximum word length that was indexed (by default 7 characters), so that you will have no trouble finding "basketball positions" (10+9 letters) or "skyscraper architecture" (10+12 letters). Just as always the components are only matched up to the length that was indexed, which is not a big problem because there are not many words other than "basketball" and "skyscraper" that start with "basketb" or "skyscra", respectively.
In fact the spaces in the search terms match unindexed word delimiters other than space characters as well, such as hyphens, so you will also find "Spider-Man" and "freeze-dried" when searching for "spider man" and "freeze dried", or underscores as in "bank_account" (think of a filename like "bank_account.html") or plus signs as in "credit+card" (e.g. common in Google search URLs when searching for more than 1 word). So in that respect index searches are now even more powerful than conventional searches.
Defining spaces as being part of words is now finally a big no-no.
NEAR combination of search hits is now supported for more than 2 selected search terms. The effect is that a search hit is listed only if any of the other selected search terms occurs nearby.
File Analysis
Block-wise hashing may allow to identify complete or incomplete remnants of known notable files that are still floating around in free drive space even if they were fragmented and the location of the fragments is unknown, to show with some or very high certainty that these files once existed on that medium.
Most suitable for selected notable files larger than a few sectors, files that are ideally compressed or at least not only sparsely populated with non-zero data and do not contain otherwise trivial combinations of bytes values that occur frequently. Good examples are zip-styled Office documents, pictures and video files. Very trivial blocks within a file that consist of mostly just 1 hash value are ignored and not hashed (the same already when creating the hash set). For quicker matching, ideally work with a small hash database and do not select a hash type stronger than MD5.
Hash sets of block hashes can be created or imported in the same way as ordinary hash sets, but are handled by a separate hash database, which internally is stored in a subdirectory of the main hash database directory. You can create hash sets consisting of the block hashes of 1 file at a time, or combined hash sets of multiple selected files. The block size is currently always 512 bytes.
Block hash matches may be found as part of volume snapshot refinements. The hash values are computed when reading from the evidence object sector-wise, and that happens at the same time when running a file header signature search if selected, to avoid unnecessary duplicated I/O, with the same sector scope. Matches are returned as a special kind of search hits. Multiple matches for contiguous block are more meaningful than isolated individual matches, as they are even less likely the result of some coincidence, and they are usually combined in a single hit. The size of all such hits is shown when listing search hits. The larger the size, the higher the evidentiary value of the match. Please note that X-Ways Forensics does not verify itself that contiguous matching blocks are in the same order as in the original file(s), but that can be verified manually, and for data that is as unique as compressed data that is most likely the case.
Ability to freely carve any kind of file within any kind of file, not just those marked with the "e" flag, with a second sub-operation of "Uncover embedded data in certain file types". Use great caution to avoid delays and copious amounts of garbage files (false positives) and duplicates.
Signatures marked with the "E" flag (upper case) are never carved within other files, to prevent the worst effects, for example MPEG frames carved within MPEG videos, zip records carved within zip archives, .eml, .html and .mbox files carved within e-mail archives, .hbin registry fragments carved within registry hives. If you know what you are doing (e.g. if you are an X-PERT), of course you could remove the E flag.
Please apply this new function very carefully and only with a good reason to specifically targeted files only, such as swap files or storage files in which backup application concatenate other files without compression. Do not apply this function blindly to all files or random files. Remember with great power comes great responsibility.
There is an option to apply the carving procedure recursively, that means to those files again that were already carved within other files. This can lead to many duplicates if the outer file at level 1 is carved too big so that files can be carved in it that were also carved at level 0 (the original file).
For situations were you want to carve embedded files that are not aligned at 512-byte boundaries in the original file, you may make use of the extensive byte-level option. In such a case one of the biggest mistakes to make would be to carve at the byte level in $MFT, which typically contains many small files stored as resident/inline, but which of course is fully processed already when taking the volume snapshot. Hence the option to always exclude $MFT at the very least.
Uncovering embedded data in various files based on byte-level file carving with the "e" flag is no longer limited to file types with a tilde ("~") method.
Prevents a crash that could occur in the 64-bit edition under Windows 8 when running the encryption test.
Gallery
For large JPEG, PNG, GIF and TIFF files, at the same time when analyzing the colors in the pictures during volume snapshot refinement, X-Ways Forensics can now optionally also create thumbnails in advance for much quicker display updates in Gallery mode later. Internal thumbnails are only created if no original thumbnails are embedded in the files and extracted at the same time, and they are actually utilized for the gallery only if auxiliary thumbnails are enabled (see Options | General).
(To discard all internal thumbnails, but keep the computed skin color percentages, you may delete the file "Secondary 1" in the "_" subdirectory of an evidence object behind X-Ways Forensics' back, when the evidence object is not currently open.)
Improved representation of videos with extracted stills in the gallery, showing all stills in a loop, to give a much more complete impression of the contents of videos without further user interaction (without having to explore them).
An alternative efficient way to review a large number of videos now seems to be this: Explore recursively, filter for videos, sort in descending order by number of child objects (so that videos with a similar number of stills are shown together), and activate Gallery mode. Watch the various video stills for each video. Proceed to the next gallery page when you are confident that no incriminating videos are represented on the current page, for example when all stills have been shown, which you will know is the case when the gallery has rotated back to the first still for each video.
"Allow auxiliary thumbnails" is now a 3-state checkbox. To disable the new representation of videos described above, you can half-check that box.
When a View window displays a picture, if limited to one such window, that window will be updated with the next picture when you hit the cursor keys in the gallery. Useful especially if the View window is centered on the second monitor if the gallery is on the first monitor, on a spanned desktop. Avoids having to press the Enter key to view the picture and another key to close the View window to get the input focus back to the gallery.
X-Ways Forensics now by default extracts embedded JPEG thumbnails from .cr2 raw files. The first extracted thumbnail becomes the preview and gallery representation of a .cr2 raw file.
File Format Support
Support for Windows.edb of Windows 8.1.
Improved support for thumbcaches in Windows 8 and Windows 8.1.
Greatly improved ability to repair inconsistent EDB databases. Several changes and fixes which improve reliability when processing EDB databases in general.
.evtx event log preview shows the username, old time and new time for system time changes.
Minor fixes and improvements for EDB and SQLite database extraction.
Reduced memory consumption of the registry viewer.
Separate file type category for spreadsheets.
New file type category "Page Layout".
New file types in the ZIP and XML families defined.
Several new and revised file type signature definitions.
Timestamps & Events
A filter for event descriptions is now available.
Improved tooltips in Calendar mode.
When in Calendar mode and not showing events, you can now select which column's timestamp should be included in the calendar. Columns that are hidden (have a width of 0 pixels) are excluded, all other columns are included. The status bar reminds you which columns are included even if not currently visible because of horizontal scrolling.
More timestamps extracted from Prefetch files.
X-Ways Forensics now outputs all entries in .evtx event log files as events. Most of these events now come with a description that includes the event source, the event ID and the record number. The record number allows you to quickly search for the record in the HTML preview if you need further details about that particular event.
Extraction of MS Windows operating system update events from DataStore.edb.
The directory browser column "Internal creation" is now called "Content creation".
Usability & User Interface
Ability to filter for duplicates of files in X-Ways Investigator, by right-clicking a given file in the directory browser with an available hash value. Actually filters for that hash value. As in previous versions, the actual hash values are not displayed in X-Ways Investigator. The same command is also used in X-Ways Forensics and supersedes the "Filter by [hash value]" command that required to right-click the cell with the hash value.
New investigator.ini option +51 prevents listing of excluded items (opposite of +31). Useful to intentionally keep users of X-Ways Investigator from seeing certain files.
Greatly accelerated loading of large registry hives into the registry viewer.
No longer loses the block definition when switching from Partition to File mode and back.
Chinese and Italian translation of the user interface updated.
Acoustic signals before shutdowns (e.g. after imaging or volume snapshot refinement) to give users a better chance to abort it if they have changed their mind.
File System Support
When taking a volume snapshot, symbolic links are now connected to their targets in the volume snapshot as so-called related files, so that you can conveniently navigate to the target by pressing Shift+Backspace. Also one of potentially several symlinks pointing to a certain target will become the related file of the target, so that you can conveniently navigate to the symlink or quickly see in the first place that one or more symlinks exist that point to a certain target, since any file that has a "related" file in the volume snapshot is marked with a tiny blue arrow next to its icon. Also the same arrow will tell you whether the target of a symlink can actually be found in the file system. If a symlink links to other symlinks, those are not recursively linked. If resolving symlink takes to long because there are many symlinks in a volume, you may safely abort that step at any time.
When taking a snapshot of volumes with Windows installations, certain reparse points (a.k.a. junction points) are now connected to their targets in the volume snapshot just like as symlinks in Unix-based file systems, so that you can conveniently navigate to the target by pressing Shift+Backspace. Also there will be a back-reference to one reparse point, so that you can conveniently navigate to that reparse point or quickly see in the first place that one or more reparse points exist that link to a certain directory, since any directory that has a "related" directoy in the volume snapshot is marked with a tiny blue arrow next to its icon. Forensic license only. Reparse points that do not get connected with their target directories will still show a comment that advises you of the target path as in earlier versions of X-Ways Forensics.
For reparse points in NTFS, File mode now shows the reparse point target information instead of the directory's empty index root.
A secondary tooltip now appears for files with a "related" file when hovering the mouse cursor over the icon, which tells you the path and name of that related file, for example the target of a symbolic link.
Improved support for volume shadow snapshot properties files of Windows 8.1.
Improved ability to write certain sectors on drive letters.
Image Support
Support for .e01 evidence file with an exotic internal chunk size of more than 0.5 MB as apparently used by default by Wiebetech Ditto devices. (Note that the standard size is 32 KB).
It is now possible to store the hash values of files in evidence file containers even when including only metadata of the files, as long as the hash value of the files have been computed already and stored in the volume snapshot.
The non-forensic version of WinHex did not write the hash value of created raw images into the text file. That will be fixed with v17.4.
Miscellaneous
New X-Tensions API function XWF_GetVSProp introduced.
Support for Unicode characters in template filenames.
New Venezuela time zone defined.
User manual and program help were updated.
Various minor improvements and some small bug fixes.[/more]

 )..
).. 

 Очень надо... Заранее благодарю!
Очень надо... Заранее благодарю! 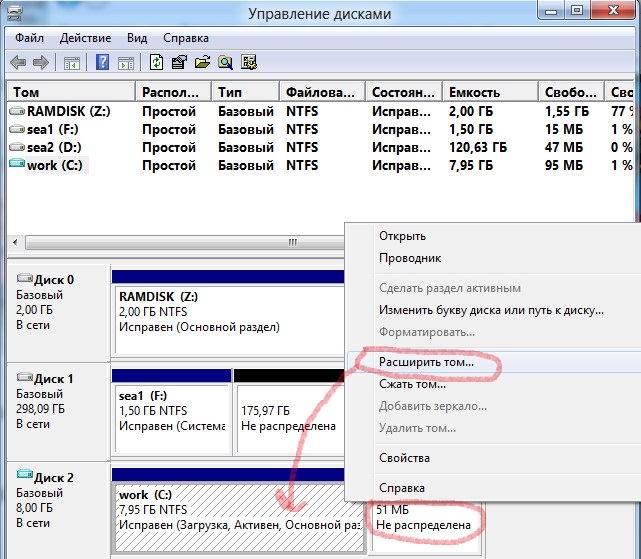 [/more]
[/more]  [/more]
[/more] 

 Хотя по идее знать бы какой там стоит акселератор и самому поправить не сложно.
Хотя по идее знать бы какой там стоит акселератор и самому поправить не сложно. 




